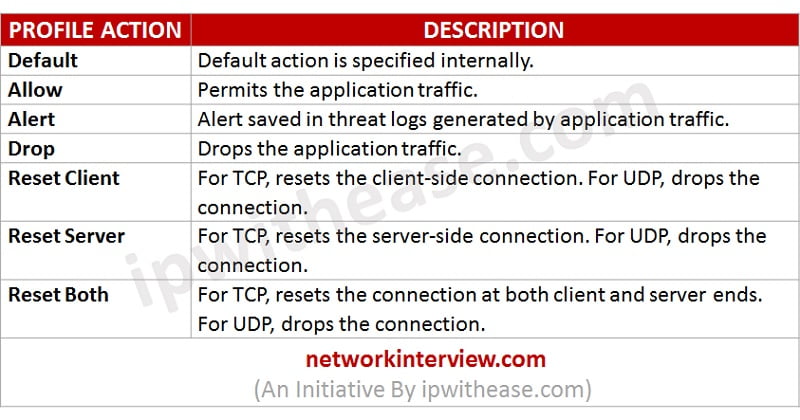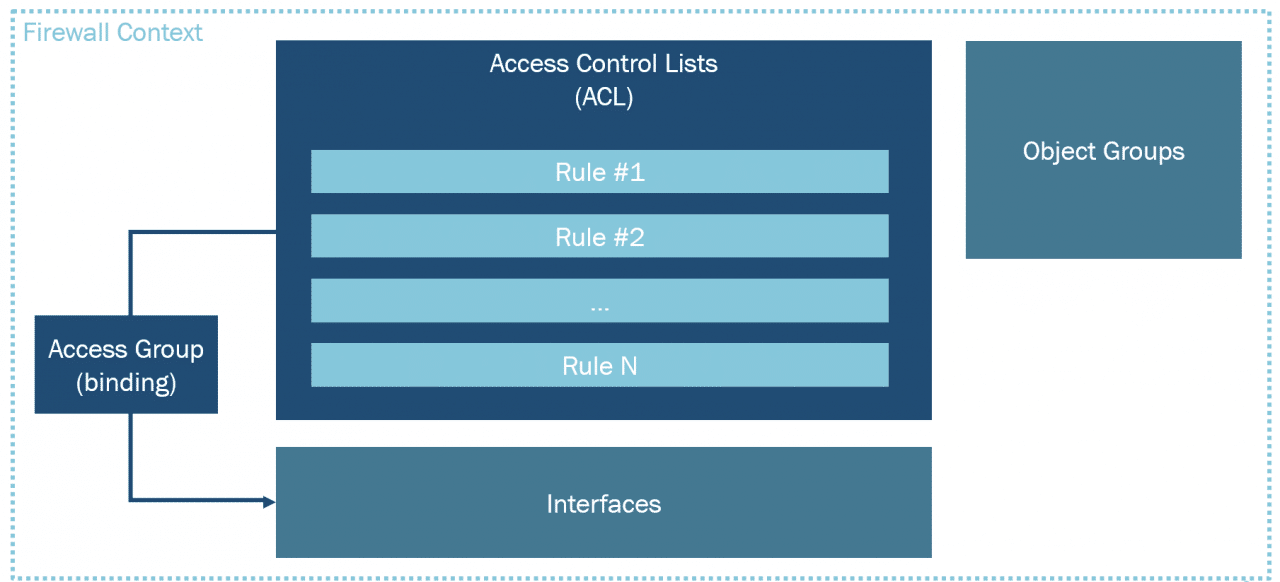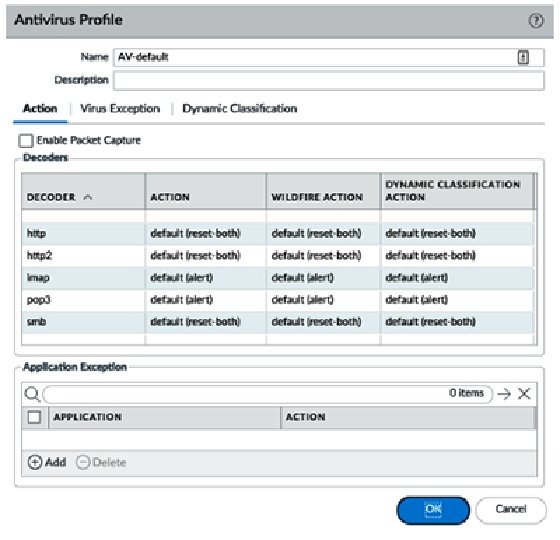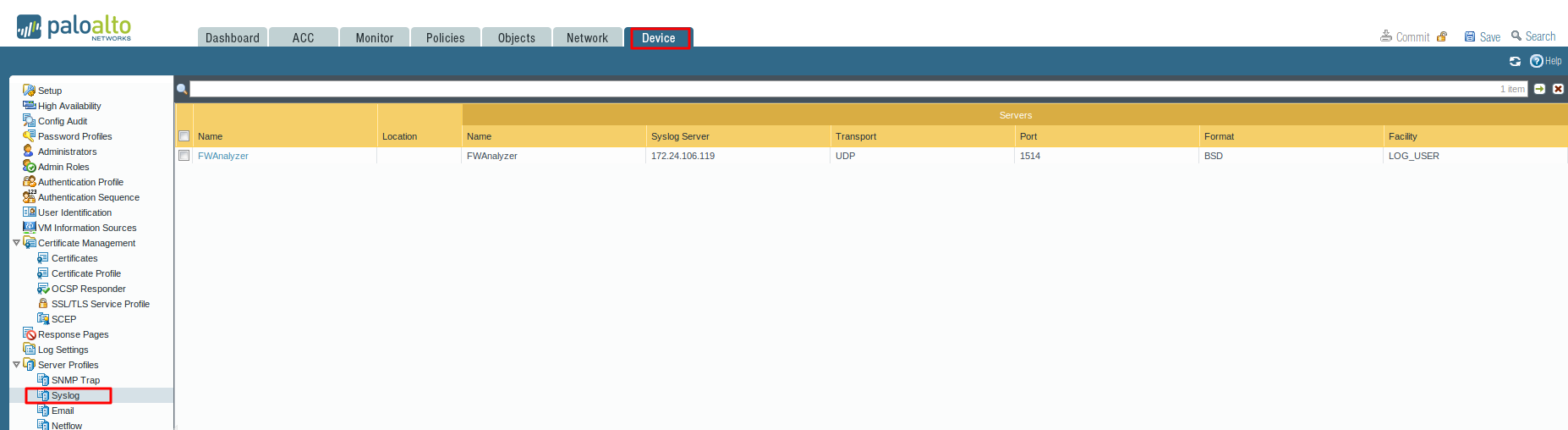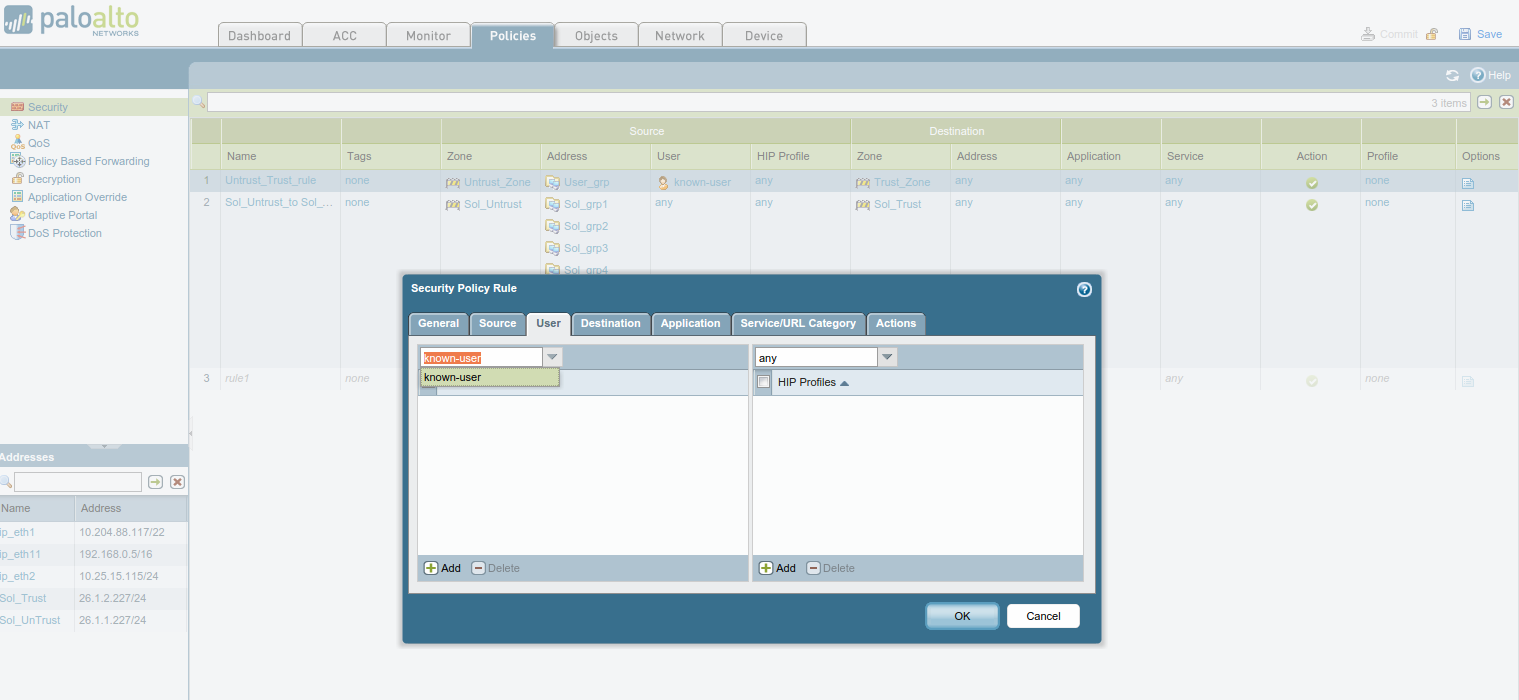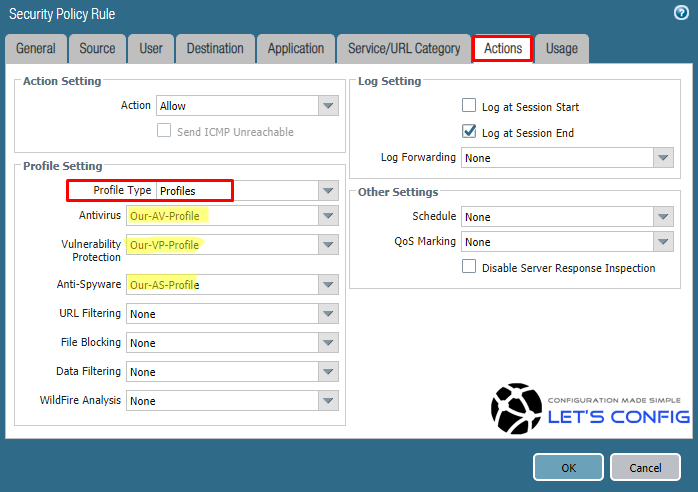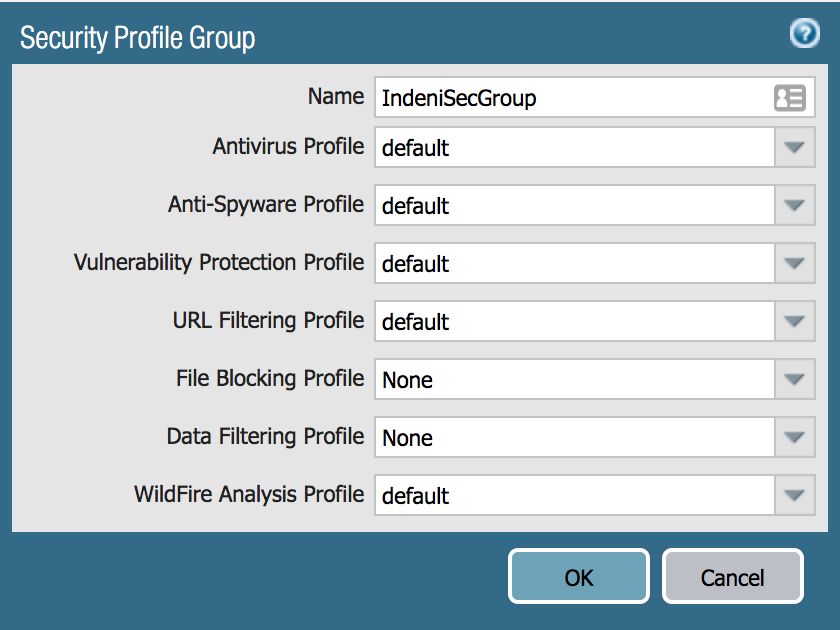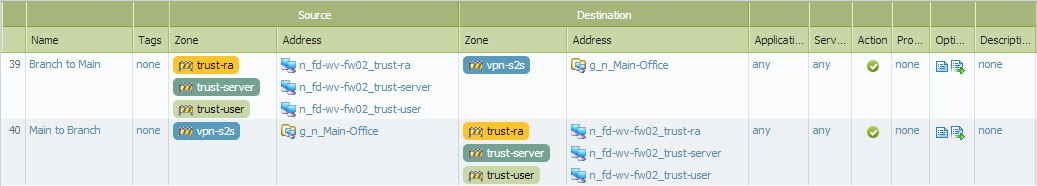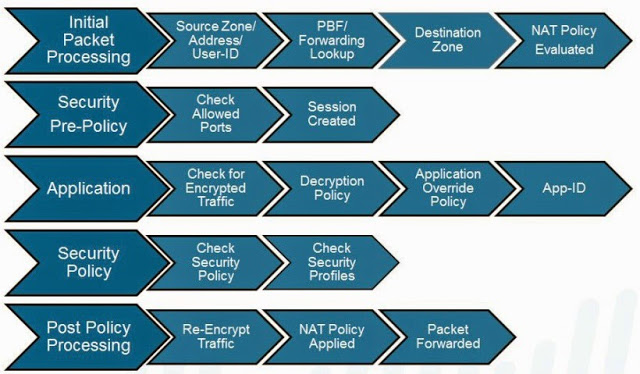
Palo Alto Firewall Application-based Policy Enforcement (App-ID), User Identification (User-ID) and Application Control Centre (ACC) Features for Enterprise Networks
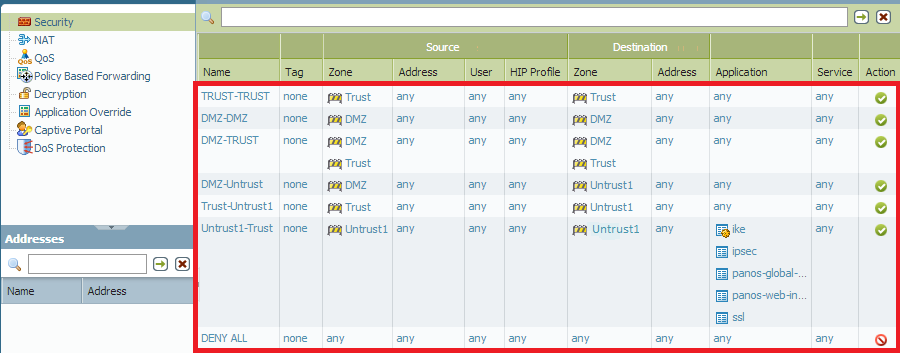
How to See Traffic from Default Security Policies in Traffic Lo... - Knowledge Base - Palo Alto Networks